Cloud Computing Adoption continues to increase. In fact, according to Gartner the worldwide public cloud services market is forecast to grow 17% in 2020 to total $266.4 billion, up from $227.8 billion in 2019; mostly driven by the increase in adoption of SaaS solutions across the midmarket. By this point, many businesses in the Greater Boston Area are considering migrating applications, data, or infrastructure to the cloud. But the biggest objection continues to be security, how safe will our business data and information be in the cloud?
To answer this, it is important to understand that cloud security is a shared responsibility between the cloud provider and the end-user business. Where both parts are equally responsible for creating layered security, one that uses proactive monitoring and artificial intelligence to respond to threats in real-time. To explain this concept better we first need to understand the different cloud security areas and who is responsible for what.
Cloud security areas, the shared responsibility model
The main objective of cloud security is to make sure the right service and the right data are delivered to the right identity, by implementing authorization and authentication controls to proactively prevent threats while staying compliant with industry regulations.
With this in mind, the shared responsibility model ensures that companies become responsible for securing what their employees do and how they interact with the cloud, while third-party vendors like AWS and Azure are held accountable for the security and upkeep of that infrastructure.
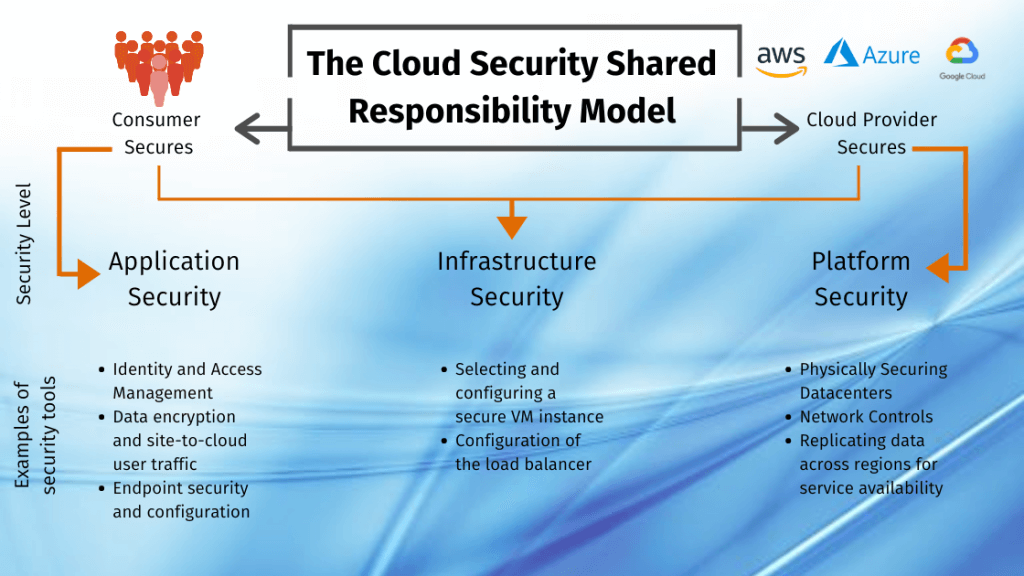
*Sources:
- Microsoft Azure, https://docs.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility
- Google Cloud, https://www.youtube.com/watch?v=MHtg2Au78LI&list=PLIivdWyY5sqLO-4ePY-A2yROgONOA6Cz4
The graph above shows the shared responsibility model with the three levels of security and the specific security actions/areas. Below you’ll find a better description of each security level and the specific technologies that can be set in place to secure your overall cloud environment.
Cloud Application Security
From phishing attacks to man-in-the-middle attacks, where connections get intercepted to access secure information, they all start with human error. The keyword here is access, you want to make sure the right identities have access to the right resources and can identify threats in real-time. The security controls here are meant to be a set of preventive actions to secure cloud data and include areas such as:
- Data encryption and site-to-cloud user traffic.
- Policies and tools for identity and access management. Implement double factor authentication.
- Endpoint security and configuration
Remember, this is your responsibility to set in place. Major cloud providers like AWS, Microsoft Azure, and Google Cloud, offer identity and access control tools; use them.
Pro Tip: When creating identity and access control policies, grant the minimum set of privileges needed, and temporarily grant additional permissions as needed. Also, consider cybersecurity awareness programs with phishing simulators and training.
Cloud Infrastructure Security
This level of security requires full transparency between both the cloud provider and the consumer. The cloud provider will make available a set of tools the consumer (business) must configure to enhance this security level. The issue here is that oftentimes this requires extensive IT knowledge to be able to configure access to VMs (virtual machines), network, and data. Which makes it difficult for small organizations to achieve it on their own.
Here is where partnering with a cloud consultant can be beneficial. Offsetting the cloud management portion to a Cloud Managed Service Provider will allow organizations to better align business goals with strategic cloud services and deploy them in such a way that they’ll be able to achieve a higher return on investment. In fact, according to Sid Nag, research vice president at Gartner “by 2022, up to 60% of organizations will use an external service provider’s cloud-managed service offering, which is double the percentage of organizations from 2018”.
Cloud Platform Security
The responsibility here is 100% for the cloud provider, who is responsible for everything from managing the physical machines and datacenter, to replicating data across multiple data centers to guarantee availability. In general, all cloud providers are under the same scrutiny from a security and compliance point of view, and each will have its own proprietary technology to strengthen the security posture of their platforms.
Cloud Security Overall
There you have it, that in a nutshell is the shared responsibility model for cloud security. To safely migrate data, applications, and workloads to the cloud, you must be confident that your cloud service provider has implemented the appropriate security measures to keep the platform secure. Additionally, to strengthen cloud security is your responsibility to use the tools a cloud service provider has at your disposal to configure security features at the application and infrastructure level, including:
- Visibility into activity within SaaS applications
- Detailed analytics on usage to prevent data risk and compliance violations
- Context-aware policy controls to drive enforcement and quarantine if violations occur
- Real-Time threat intelligence on known threats and detection of unknown threats to prevent new malware insertion points
Our cloud consulting team is ready to give you advice on building a cloud strategy that works for your business and that enhances every level of security, to not only guarantee a seamless cloud journey but also a safe one.
