If someone asked you, “what’s it like to work at [your company]?”, what would you reply? I suppose it depends on your role, how long you’ve worked there and the impression you want to relay, but it’s safe to assume that some aspect of your answer would include elements of culture.
“Culture” can seem like a fuzzy concept, but its definition does help pin to unpack it.
“Culture is the total way of life of particular groups of people. It includes everything that a group of people thinks, says, does and makes — its systems, attitudes, and feelings. Culture is learned and transmitted from generation to generation.”
In this post we’re talking about an important subset of corporate culture; we’re analyzing and providing tips on how to shape “attitudes” and “behaviors” towards cybersecurity.
An effective cybersecurity culture enables a virtuous circle where employees, understand their roles and responsibilities for protecting their firm, literally becoming human firewalls.
For instance, Julia who works in Marketing is doing some research into venues for an event. She’s on a reputable website she’s used multiple times, only this time she clicks on a link that takes her to a sketchy page. Immediately she closes the window, disconnects from the network, turns off the laptop, and communicates the case to IT. In this case, Julia’s prompt reaction allowed the company to respond in a resilient manner by speeding up its response and recovery cycle.
Therefore, the real question is, how can organizations nurture a workplace where everyone acts like Julia? How do we build and maintain a cybersecurity culture within our organization?
Research by MIT Sloan School of Management and Carnegie Mellon University found four pillars for a thriving cybersecurity culture:
1. Increase Training Budget and Identify Relevant KPIs
According to the Cybersecurity Survey by ISACA and CMMI Institute, today 86% of SMBs in the U.S. have a budget for improving cybersecurity. but only 38% of those businesses invest in practices that fundamentally shape cybersecurity culture.
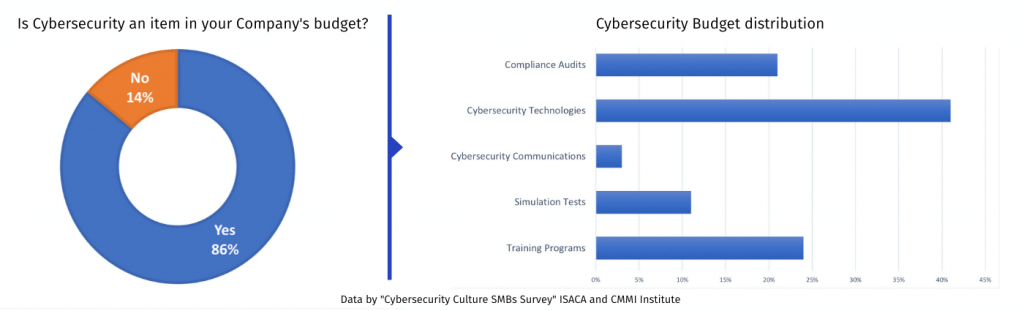
When considering how to address cyber threats, most funds go towards software and hardware that are part of a layered approach to cybersecurity, and only a few organizations are investing in training programs, such as phishing simulators, to encourage safe user behavior.
And of the few SMBs that are funding employee training programs, few are actively measuring success. A simple fix is to fund training and for leadership to indicate a metric that correlates to a safer culture.
For instance, if a firm uses phishing simulators to test its people, a KPI could be the click-through rate of malicious links.
2. Reward Followers of Policies and Protocols
Just as we may have a dress code for the office, having a cybersecurity manual will provide structure to our organization’s stance on cybersecurity best practices. However, this step goes beyond writing policies and procedures posted on a pinboard.
We should complement it with a rewards program, where employees get recognized by owning and following cybersecurity policy.
Workplace recognition not only motivates but also provides a sense of accomplishment and belonging. To strengthen a cybersecurity culture, organizations should rely on programs that provide employee recognition, boosting individual engagement around cybersecurity best practices that collectively change the mindset.
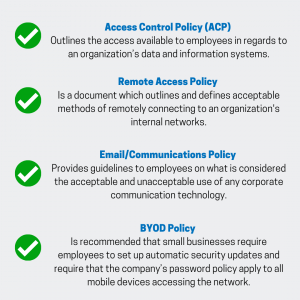
Here are some policies and protocols you should be considering, but remember, these must be tailored to your organizational culture.
3. Training, Training, Training
The “Break Room Training” model was for years the best choice for most types of staff training. We would gather as many employees into a room, order bagels, give a lecture with slides, etc. p. It was easy, concrete in the messaging and it seemed to work.
Only, it doesn’t really work. A PowerPoint won’t encourage safer cybersecurity culture.
Unfortunately, security awareness training is only effective when people become more cautious continuously, and people don’t become careful overnight.
So how can we deliver training that really drives behavior change? The answer: Integrated Security Awareness and Simulated Phishing Platforms. Knowbe4 or Hook Security are the most used tools for this purpose, as they successfully combine four types of training, making the message cohesive and using different techniques to change behavior.
- Interactive browser-based training: On-demand interactive training gives users a fresh new learner experience that makes learning fun and engaging.
- Custom phishing simulations: These platforms offer the ability to customize fake phishing emails adding learning video content to increase awareness of the issue and ways to proceed.
- Skill-based assessments and surveys: The level of cybersecurity awareness won’t be the same across all employees, those in IT might feel more confident in detecting a phishing attack and will require a different type of simulation than someone in Sales. In addition, as surveys prove to be a great way to assess the level of our cybersecurity culture is important to have platforms that can analyze data and take action accordingly.
- Rewards and champions programs: This goes a long way when making cybersecurity the “Hot Topic” amongst employees, these programs create a sense of unity across the entire organization and are a great way to reinforce policy and best practices.
Specialized training is necessary to create an agile and responsive workforce that can recognize and respond appropriately to new cyber attack methods. Even when individuals are aware of potential risks, they may not be equally familiar with the best response or solutions.
Note: When considering a security awareness and simulated phishing platform, make sure you are covering all the areas and not just activating a single type of training, this is key to a successful cybersecurity awareness program.
4. Communications Strategy
This is all about creating transparency and trust, and it plays an important role at all stages of a cybersecurity strategy: before, during, and after an attack.
Before: Building awareness and a culture of learning
Successful communication is a two-way street—one that usually starts with listening. Our employees SHOULD be encouraged to speak up if they’ve mistakenly clicked on a malicious link or downloaded a file that seemed suspicious. They need to know they won’t be punished but that their quick response has helped the organization to recover and alert other users of the potential threat.
Directing IT to share examples of successful or thwarted attacks leverages a positive aspect of group psychology and social norms, as employees feel more invested in the shared responsibility for their online behavior, which in turn strengthens the overall cybersecurity culture.
During and After: We’ve been breached. Now what?
The goal of any organization is to avoid being a victim of a cyber-attack. But hoping for the best sometimes doesn’t do it. Having a communications protocol to maintain transparency during and in the aftermath of an attack is essential to build trust. This includes sharing with stakeholders what steps the company is taking into remediating and making sure the attack doesn’t interfere with the business continuity.
Communication might be the last pillar but can be one of the most important. How would we know what type of awareness training to do, or what customization our phishing tests need if we aren’t listening to the legitimate cybersecurity concerns and behaviors our employees are currently having? So in a way having a good communication strategy is fundamental to building a cybersecurity culture.

