You’d be shocked at just how vulnerable we are to phishing attacks.
The most eye-opening 2019 phishing statistic from the Verizon DBIR is out and should serve as a warning to CEOs, business leaders, and concerned employees alike. Phishing scams were the number one threat agent used in connection with social engineering and malware attacks.
Across all industries, untrained employees in small businesses face an average 30% phishing vulnerability percentage based on a study from KnowBe4.
Some of you may be thinking “this won’t happen to me!” but it’s time for a wake up call, because even if you’re aware of scams and what to look out for, your colleagues may not be, and so your job and company are at risk unless we make a serious change.
But wait, there’s hope!
In this article, we’ll not only share the industry benchmarks, but I’ll explain how you can improve your firm’s phishing alertness by 92% or even more.
Let’s dive right in.
What is Phishing and How Does it Work?
Phishing is a form of cybercrime typically initiated through a disguised email with the ultimate goal of obtaining sensitive information (usernames, passwords, credit card details) from its target(s).
Social engineering is a key component to successful phishing attempts. Phishing emails, links, or attachments are presented in a convincing, relatable, and familiar fashion leading the user into believing it is coming from a trusted source.
Depending on the desired outcome and target, phishing attacks present many forms:
- Classic phishing: Using this method, hackers cast a “wide net” by sending mass emails to targets hoping a small percentage of the users expose their private credentials.
- Spear phishing: A highly specific, pointed form of a phishing attack intended to extract sensitive information from an individual or small group. Often, hackers research their targets extensively in order to customize the attempt and ensure a higher chance of exploitation.
- Whaling phishing: In reference to the large size and power of the whale, ‘whaling phishing’ refers to the attempt to use email spoofing and social engineering to target the biggest players in the game: high ranking business leaders and powerful CEOs. The end goal of this form of phishing is to initiate a large wire transfer to the hacker’s bank account.
- Ransomware Phishing: Everyone in an organization can be targets of a ransomware phishing attack. Once an employee clicks on a link or attachment, malicious code is downloaded onto their computer and can infect the entire organization’s network. Once hackers seize the network, they shut it down and demand a hefty ransom to be paid in order to “unlock” access back into the system. Other times, hackers find embarrassing photos or scandalous communications and use this to leverage big payments from guilty parties. Ransomware attacks can be financially and emotionally crippling for any organization.
- Domain-Spoofing Phishing: This form of phishing typically spoofs a high ranking business leader or CEO email in order to target lower-ranking employees. When receiving an email from a manager or CEO, employees overlook red flags in order to please a nonexistent order from an authority figure. Oftentimes, employees are tricked into transferring large sums of money per the CEO’s orders.
Other variants of phishing attacks exist, but these are some of the most common. It’s important to note that phishing will continue to evolve and therefore recurring employee training is essential for staying on top of the latest trends. Hackers have more recently been deploying attacks via SMS text messages (SMS phishing) and vishing (voice phishing). Industry leaders predict that phishing will even evolve to deploy ‘deepfake’ technology (simulated video phishing.)
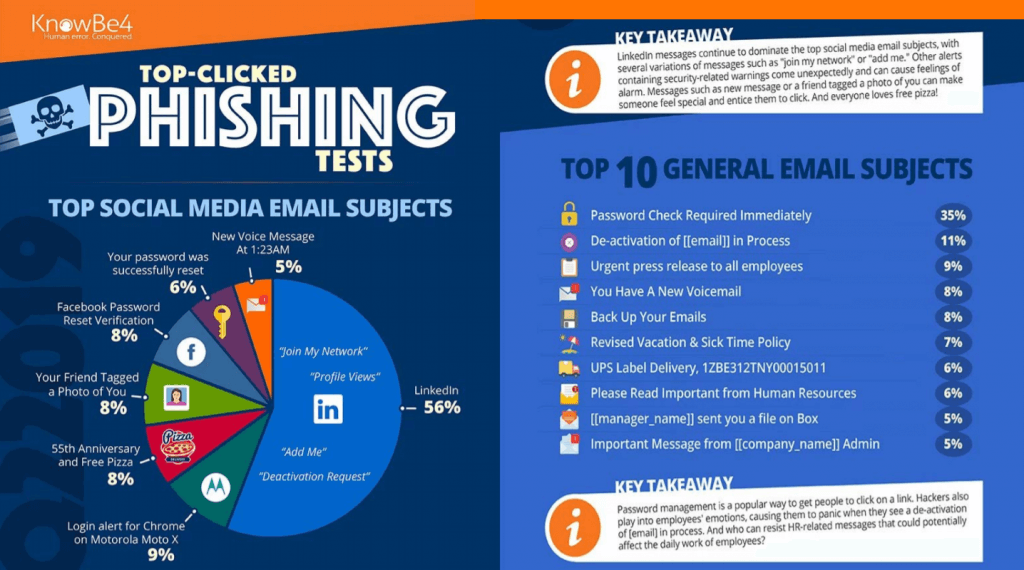
Baseline Phishing Prone Percentage by Industry
PPP (Phish-Prone Percentage) is a metric which identifies just how vulnerable people are to phishing attacks. The following industry statistics were gathered from phishing tests where over 9 million unique employees were sent an email containing a fake phishing link. The PPP illustrates the percentage of employees who fell for the test and clicked the link without training or advance warning. This base vulnerability percentage serves as a great tool to assess a starting off point.
Note: small companies are defined here as having 1-249 employees.
Construction
Who would ever guess that the construction industry is at a 38% vulnerability percentage for phishing attacks and the smaller companies even higher?.. Construction companies are an attractive target for hackers because they store a lot of private data on potentially outdated networks, they hold vendor information, architectural blueprints, financial information, consumer data, proprietary information and assets, and key stakeholder information for projects. It’s no wonder that hackers see them as an easy target.
Consumer Services
While the consumer services industry is incredibly diverse: encompassing food production, packaged goods, pharmaceuticals, clothing, electronics, etc., it is practically a goldmine for any criminal. Consumer credit card data, amongst email addresses, phone numbers, and addresses may be used for immediate financial gain or for further exploitation by organized crime. Consumer services employees stood at just above 36% phishing proneness. The risk was highest for smaller and medium-sized consumer service companies: being 36.3% and 33.3%, respectively. Protecting consumer data must be prioritized in this industry.
Insurance
Small and medium-sized insurance companies stood at heightened risk for phishing attacks in 2019, with small businesses testing at 36.4%. Many small insurance companies lack an emergency response protocol in the case of a breach. They may also lack strong internal security and may be using out of date software spread across multiple subsidiary offices.
However, hackers see the insurance industry an attractive target due to the incredibly sensitive health data they store. SSNs, payment methods and accounts, medical records, asset information, and even beneficiary information may be incredibly valuable to criminals.
Manufacturing
Small and medium-sized manufacturing companies are at the highest vulnerability rate for phishing attacks and average a 35% PPP. Organized criminal organizations are increasingly targeting the manufacturing industry for financial gain. Large-scale or “classic” phishing campaigns allow criminals to collect not only important financial information about employees, vendors, and customers, but it allows hackers access to invaluable intellectual property.
For example, criminals from other parts of the world may target American manufacturing companies for their innovative blueprints and manufacturing design. Once they gain access to blueprint and machine data, they are easily able to replicate it back home to then sell to a willing buyer. In some cases, business competitors may pay cybercriminals to phish for network entry in order to plant malware which shuts down machinery.
Talk about petty competition!
How to Improve Phishing Resiliency
Insist on Long-Term Training Initiatives
According to KnowBe4, after one year of CBT (computer-based training) and phishing simulations, only 2% of employees remained vulnerable to phishing attacks across all industries, which is a 92% improvement!
Small and medium-sized businesses made the most significant improvements with ongoing education and frequent, monthly testing. On average across industries, small businesses started at a base of 33.5 and within 12 months reduced their failure rate to a 1.9 PPP. Medium businesses started at a base of 31.9 PPP and dropped to a 2.2. Please refer to the figure below for a simple visual breakdown of the net reduction in vulnerability.
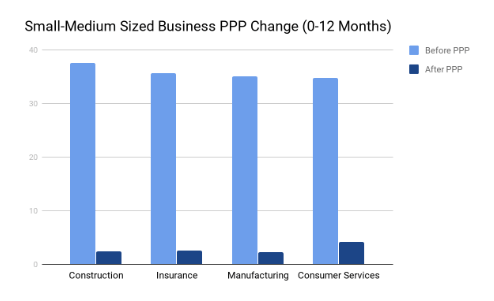
As the chart reveals, improvement after one year is entirely feasible after undergoing a thorough vulnerability assessment, identifying areas of improvement to combat phishing, and recurring employee training. It’s best to first begin by assessing your current security protocol. Could your current security be improved? Have you started any employee training at all? What about removing all public data containing your email domain from search indexes?
Make Security Training “Edutaining”
According to Brad Powell from Hook Security, training should be fun! A successful twelve-month training program should spark excitement, fuel engagement, and create a lasting impact on your employees so they remain alert. It shouldn’t become a chore. Instead, a training program can become a source of intellectual curiosity, ongoing discussion, and learning. Try showcasing live phishing demos, presenting common phishing traps, and playing scenario-based decision-making games. The more simulations and real-life scenarios are presented to employees, the more likely they will act in a safe manner when presented with a real phishing attack.
Long Term Training Tips
Pointer #1: Assess your current technical security
In order to maximize the success of long term training, it’s a good idea to assess what vulnerabilities exist in your current technical security.
- Make sure that your employees cannot download external programs at their own discretion. If even one employee downloads a malicious attachment or .exe program, ransomware could be downloaded across the entire system.
- Ensure your employees change their passwords as frequently as once a month. Ensure they are using the strongest passwords possible and that they use multifactor authentication.
- Encrypt all storage devices.
- Use the best web filters to prevent employees from visiting unsafe websites.
- Install email filters which detect and block spam from entering into the main email inbox.
Pointer #2: Rewarding successes
- Instead of only pointing out your employer’s mistakes, make sure to reward their successes as soon as you notice it. Not only will rewarding successes strengthen team building, but it will help reinforce good critical thinking.
- Management should be sure to reward good action because most preventative action goes unnoticed. Training shouldn’t be associated with negativity, instead, it should be as positive and educational as possible.
- Acknowledging and reinforcing employee success can be as simple as a verbal acknowledgment, a congrats email, or a simple token of appreciation. Think about how much an employee could save your organization by responding appropriately. Thank them!
- Management should not hesitate to deliver this positive reinforcement on an individual basis.
- Since the fate of a company could quite literally rest on an individual, it’s important to personally congratulate someone for their hard work and awareness responses. If an individual is underperforming, it’s great to offer them tailored assistance to get them on track. Don’t let any individuals slip through the cracks.
All of this advice is best used when pairing it with the best support possible. Using a dependable, trustworthy, and results-driven MSP is critical towards ensuring your company is phish-proof. At Casserly Consulting Cyber Security Services, any Massachusetts business can claim a completely free, no strings attached vulnerability assessment. What’s stopping you from ensuring a more secure tomorrow for your company? Give us a call or email today and we’d be more than happy to answer any of your questions.